
DAPS Project
Privacy is a right, not a privilege
FAST ACCESS LINKS
Project Introduction
Statement of the problem
 In traditional blockchains and various “paral” anonymity chains,the users are exposed to analytics and malicious attack vectors. Many around the world use this exposed data to exploit cryptocurrency users.
In traditional blockchains and various “paral” anonymity chains,the users are exposed to analytics and malicious attack vectors. Many around the world use this exposed data to exploit cryptocurrency users.



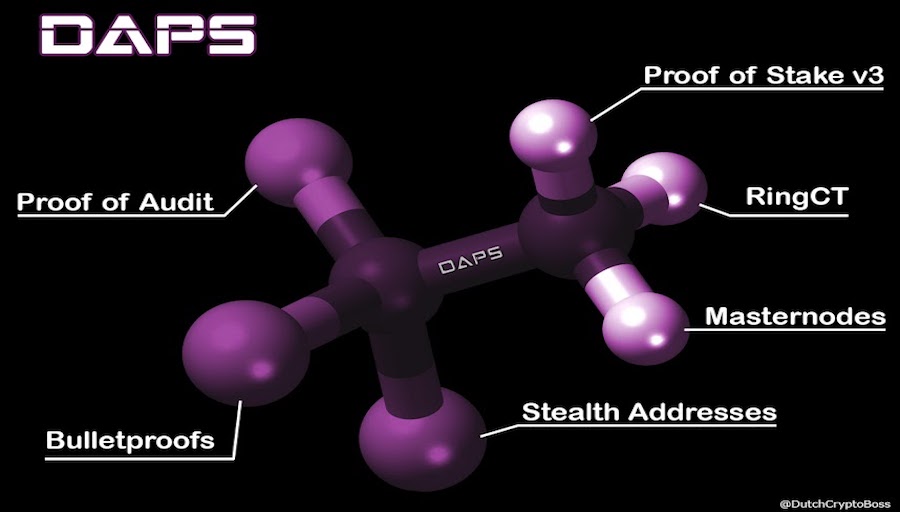

DAPS IS DIFFERENT. HOW?
DAPS utilizing several key technologies:
Ring CT
Bulletproofs
Stealth Addresses
Stealth Transactions
Proof of Audit
This mix of features, featuring Proof-of-Audit- which we call “The Harpocrates Protocol” – creates a completely trustless anonymous blockchain network. Focus is given to the privacy of a users. DAPS is anonymous with hidden transaction amounts. But this presents a specific problem when collateralizing a Masternode and ensuring that the collateral is correct and locked away. Therefore all collateralization transaconsfor Masternodes have a visible amount that is neither Bulletproofed nor part of a Ring signature either.
More technical information you can read on Whitepaper of the project.
MAIN SPECIFIC FEATURES OF THE DAPS CHAIN
RINGCT
Ring Confidential Transaction (RingCT) is a way of mixing in a real transaction with a predetermined number of fake transactions. The Ring size determines the number of additional fake transactions that are added. The actual transaction is hidden within a mixture of fake transactions. Monero’s ring size currently is 11, but DAPS will have a randomly generated ring size within given range 6-12
BULLETPROOFS
Bulletproofs are short non-interactive zero-knowledge proofs that require no trusted setup. For example, prove that an encrypted number is in a given range, without revealing anything else about the number. Bulletproofs are designed to enable efficient confidential transactions in Bitcoin and other cryptocurrencies.
STEALTH ADDRESSES
With DAPS chain if a sender wants to send to a recipient, the recipient’s public address will then be used for generating a one-time generated public key/address. Such private key can only derive by the owner of the public address, who has both pairs of private keys in DAPS dual-key system.
DUAL-KEY SYSTEM
DAPS use a dual key system to provide stealth addresses to obfuscate addresses. A public address is derived from a private view-spend key pair. A public address can contain optionally payment ID, which is usually used by exchanges.
STEALTH TRANSACTIONS
The Public address/integrated address of the receiver for a transaction should be sent to the sender, whose wallet does the following steps to create a fully private transaction:
Parse the public address to extract public view key Pv, public spend key Ps, and payment ID (optional) of the receiver
Check whether the wallet has enough balance to send
Generate a one me-generated public key P for the receiver
Create a transaction output with destination as the above one me-generated public key and the expected sending amount
Select a set of spendable UTXO to be transactions inputs
Generate ring signature
MORE DETAILS ABOUT =>
MASTERNODES AND STAKING NODES ON DAPS
POA AND POS CONSENSUS DETAILS
TOR/OBFS4
OTHER FEATURES
READ HERE (PAGE 13-15)
